Mikrotik RouterOS配置原生IPv6
缘起
随着现在公网IPV4越来越难获取,为保障内网各项服务的公网访问通过配置IPV6服务来满足需求,为防止遗忘记录下过程。
更新情况
- 由于Mikrotik对V6支持性仍在不断更新中,本文记录内容随时更新
- 目前更新时间为2025年03月01日。
- 当前RouterOS支持SLAAC方式IPV6,DHCP方式暂时只支持通告前缀信息,不能分发地址。
RouteroS说明
根据 Mikrotik 官方文档,目前 RouterOS能较好的支持以SLAAC方式来配置IPv6,而 RouterOS 的 DHCPv6 暂时只支持通告前缀信息,不能分发地址。
1. 获取IPV6前缀
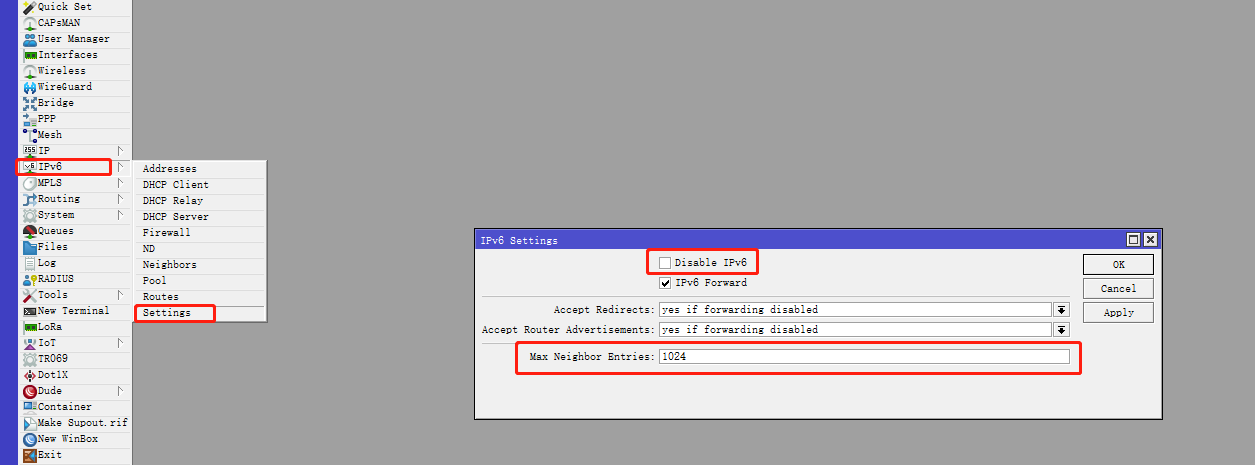
使用 Winbox 登录 RouterOS ,点击左侧导航 IPv6 菜单的子菜单 Settings 。
-
取消勾选 Disable IPv6 ,表示开启 RouterOS IPv6 相关功能。
-
并将 Max Neighbor Entries 参数(类似于 ARP 表最大条目数)修改为合适的数值,演示为1024
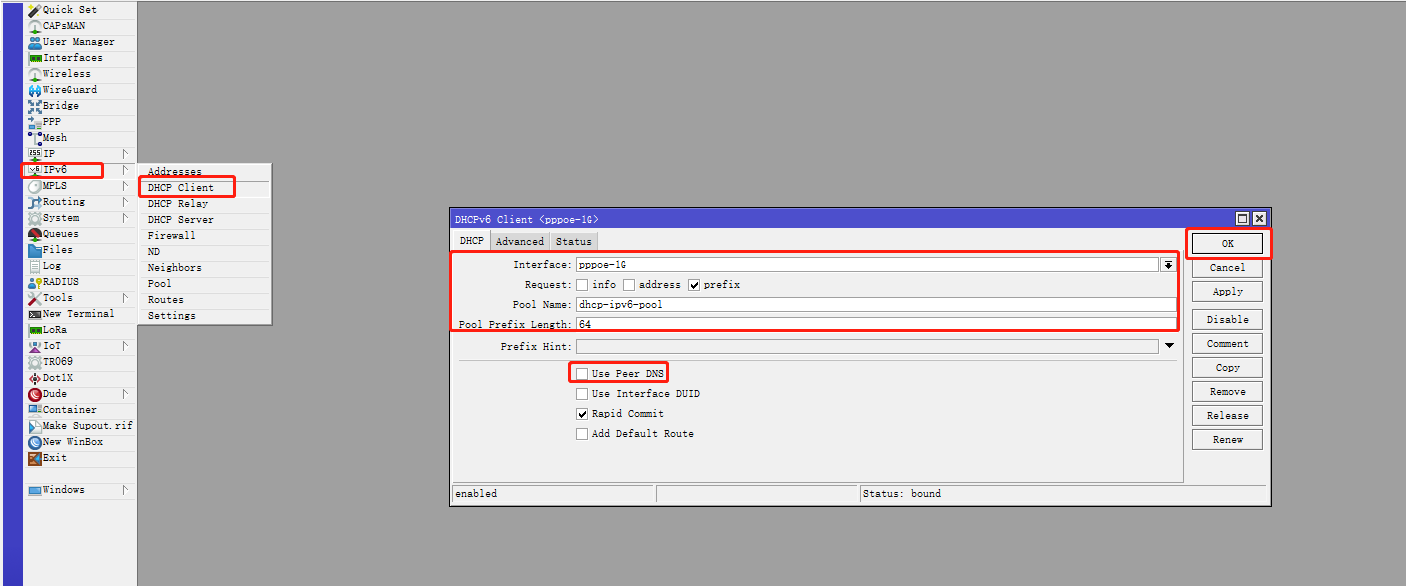
点击左侧导航 IPv6 菜单的子菜单 DHCP Client ,点击 + 按钮。
| 参数 | 值 | 说明 |
|---|---|---|
| Interface | pppoe-out1 | 从 PPPoE 拨号中获取 IPv6 前缀 |
| Request | prefix | 表示只获取前缀信息 |
| Pool Name | dhcpv6-gua-pool1 | 设置本地 IPv6 地址池名称 |
| Pool Prefix Length | 60 | 设置本地 IPv6 地址池长度 |
| Use Peer DNS | 取消勾选 | 不使用运营商的 IPv6 DNS |
| Add Default Route | 不勾选 | 是否加入默认路由,建议是无需勾选 |
| Comment | defconf: local DHCPv6 client | 备注信息 |
| Pool Prefix Length | 参数默认值为 64 | 该参数与运营商相关,建议与运营商提供的参数保持一致。 |
国内环境,该参数一般为 56 、 60 、 64 ,不同的 Pool Prefix Length 将影响内网 IPv6 子网数量。
国内运营商 Pool Prefix Length 参考如下,欢迎提交信息。
| 运营商 | 值 |
|---|---|
| 电信宽带 | 56 |
| 移动宽带 | 60 |
| 联通宽带 | 60 |
对于 Add Default Route 参数,没有相关 RFC 文档表明 DHCPv6 Client 在仅获取前缀时需要添加默认路由。
经过测试,该选项勾选与否均不影响后续设置以及 IPv6 的网络访问。
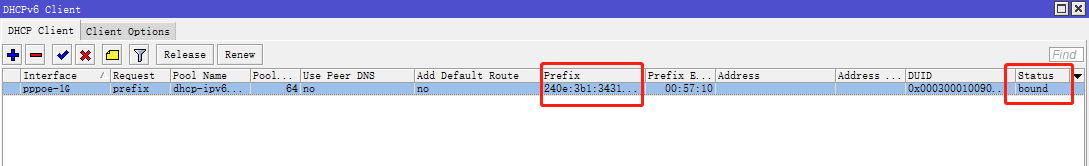
DHCPv6 Client 创建完成后,如果正确获取到了 IPv6 前缀信息,将如图所示。
如果未获取到前缀信息,尝试让 PPPoE 重新拨号。
如果在重新拨号后,仍未获取 IPv6 的前缀信息,那么运营商可能并未提供 IPv6 接入能力。
2. 设置接口 IPv6 地址
在设置接口 IPv6 时,拨号接口 pppoe-out1 是 无需 分配 IPv6 公网地址的。
只需给网桥接口 bridge1 分配一个 IPv6 GUA 公网地址,并附加一个 IPv6 ULA 私有地址即可。
注意:
当前 RouterOS IPv6 还未设置防火墙,给内部接口分配公网 IPv6 之后,RouterOS 相当于已经与公网互联。
如果当前 RouterOS 有不完善的安全设置(比如使用了弱登录密码),系统存在被入侵的风险。
因此建议先关闭 DHCPv6 Client ,直到 RouterOS IPv6 防火墙等内容设置完成后,再将其打开。
3. 分配 IPv6 公网地址
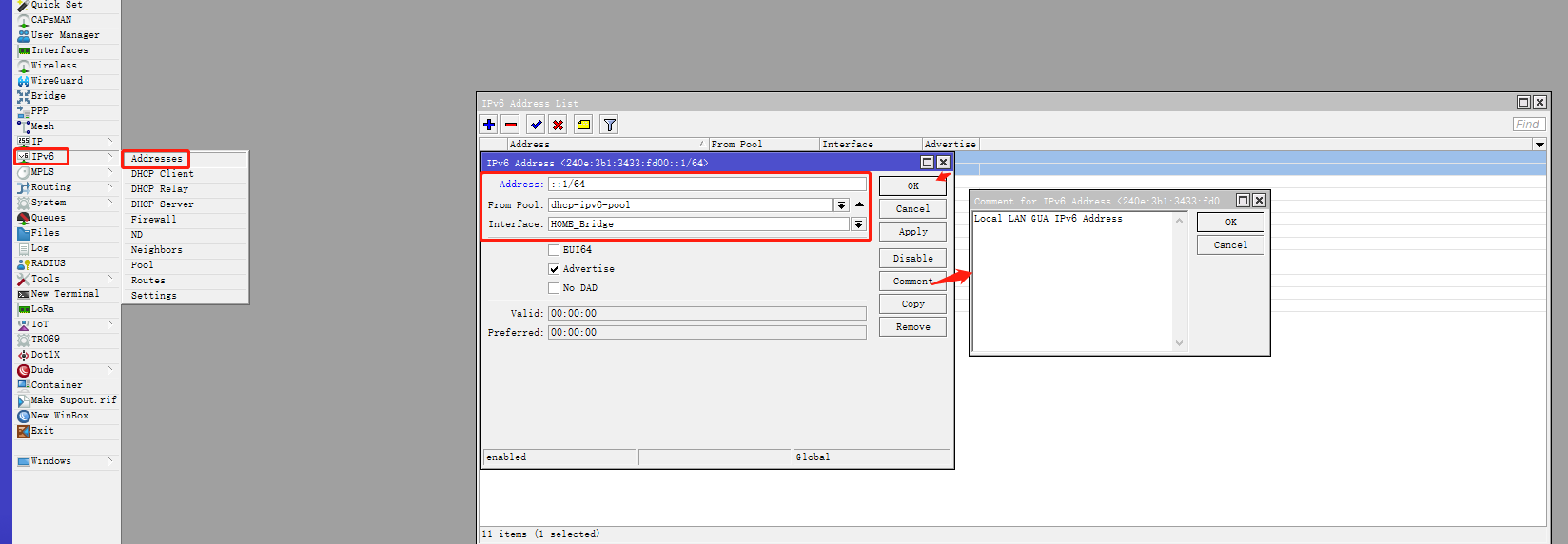
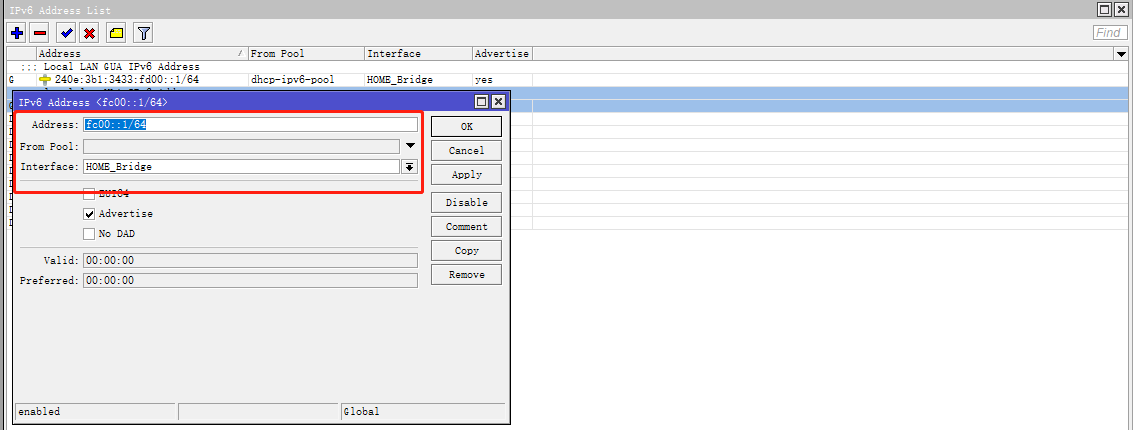
点击 Winbox 左侧导航 IPv6 菜单的子菜单 Addresses ,点击 + 按钮。
| 参数 | 值 | 说明 |
|---|---|---|
| Address | ::1/64 | 自动匹配前缀,前缀长度 64 ,并使用顺序第一个地址 |
| From Pool | dhcpv6-gua-pool1 | 选择 DHCPv6 Client 中创建的地址池 |
| Interface | bridge1 | 选择内部网桥接口 |
| Advertise | 勾选 | 勾选该选项,内网设备将生成公网 IPv6 地址 |
| Comment | defconf: local LAN GUA IPv6 address | 备注信息 |
4. 分配 IPv6 私有地址
根据 RFC4193 - Unique Local IPv6 Unicast Addresses 中给出的定义,IPv6 ULA 私有地址前缀为 FC00::/7 。
该前缀包含 FC00::/8 和 FD00::/8 两个部分,严格意义上 ULA 目前应该使用 FD00::/8 。
在实际使用场景下,建议使用类似 RFC4193 IPv6 Generator 的工具来生成符合规范的 ULA 私有地址。
该工具只需要输入接口(例如 RouterOS 的 bridge1 )的 MAC 地址即可。
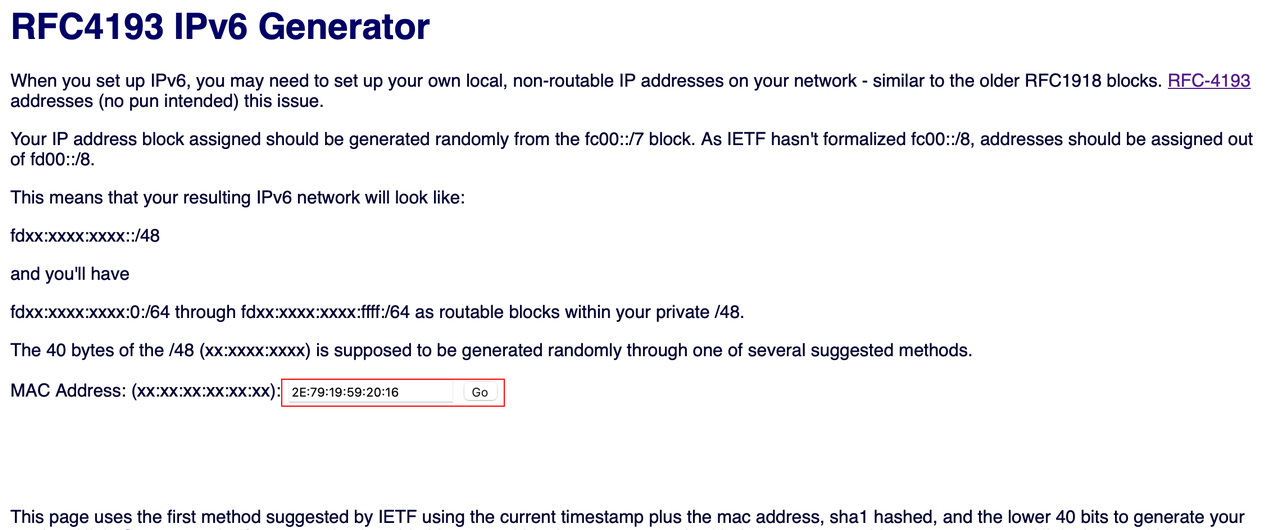
得到符合规范的 ULA 私有地址,如图所示。

回到 Winbox ,再次点击 + 按钮。
| 参数 | 值 | 说明 |
|---|---|---|
| Address | fdac::1/64 | 指定前缀,前缀长度 64 ,并使用顺序第一个地址 |
| Interface | ridge1 | 选择内部网桥接口 |
| Advertise | 勾选 | 勾选该选项,内网设备将生成私有 IPv6 地址 |
| Comment | defconf: local LAN ULA IPv6 address | 备注信息 |
注意:方便起见,本文使用 fc00::/64 作为演示。
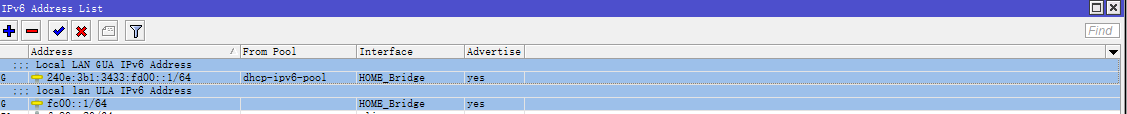
DHCPv6 Client 正确获取 IPv6 前缀,并且内部网桥 bridge1 两个 IPv6 地址均添加完成后,如图所示。
5. 设置 ND 服务前缀
点击 Winbox 左侧导航 IPv6 菜单的子菜单 ND 。
在 Neighbor Discovery 对话框中切换到 Prefixes 选项卡。
这里可以看 Prefix 列表中的 fdac::/64 被标记为 D ,表示该条目为 “自动动态生成” 条目。
点击 Default ,修改 Prefix 的有效期。
根据 Systemd.Network 中的描述:
Preferred and valid lifetimes for the prefix measured in seconds.
PreferredLifetimeSec= defaults to 1800 seconds (30 minutes) and
ValidLifetimeSec= defaults to 3600 seconds (one hour).
经过一段时间的测试,将 Preferred Lifetime 设置为 1 小时,将 Valid Lifetime 设置为 2 小时较为可靠。
| 参数 | 值 | 说明 |
|---|---|---|
| Valid Lifetime | 02:00:00 | IPv6 地址最大有效期 |
| Preferred Lifetime | 01:00:00 | IPv6 地址建议有效期 |
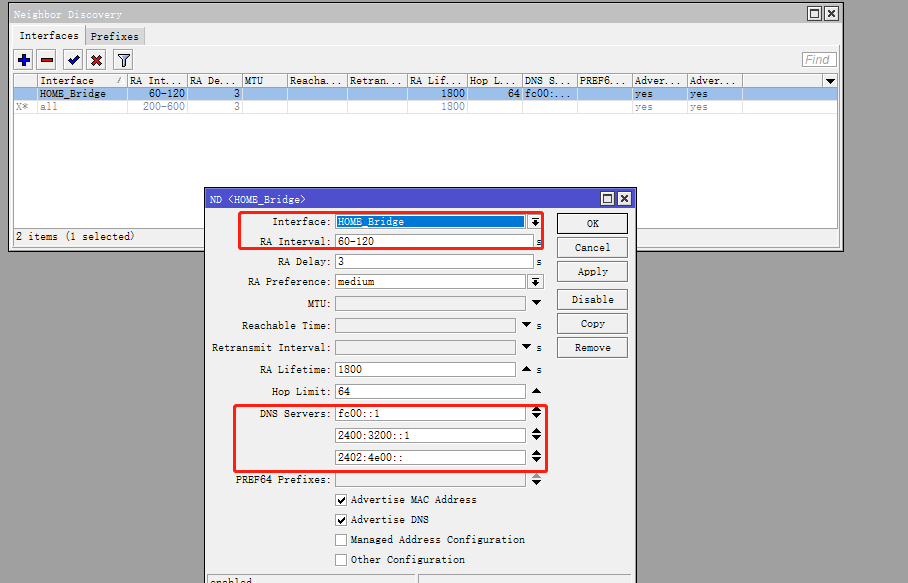
6. 设置ND通告
在 Neighbor Discovery 对话框中切换到 Interfaces 选项卡。
鼠标 单击 选中 Interface 为 all 的条目,点击 × 按钮将其禁用。
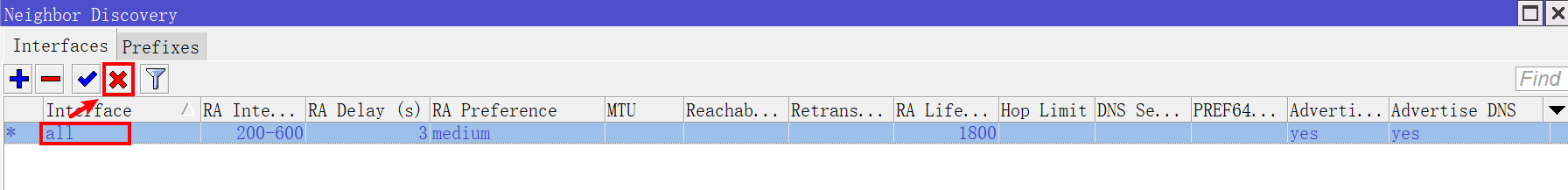
点击 + 按钮,新增一个 ND 通告配置。
如果内网环境中 没有 自建 DNS 服务器,则可以将 DNS Servers 参数设置为 fdac::1 ,与 bridge1 的 ULA IPv6 地址相同。
| 参数 | 值 | 说明 |
|---|---|---|
| Interface | bridge1 | 选择 ND 通告使用的接口 |
| RA Interval | 60-120 | 设置 ND 通告的时间间隔,时间单位为秒 |
| Hop Limit | 64 | 缺省情况下,由设备初始发送 IPv6 单播报文的跳数限制是 64 |
| DNS Servers | fdac::1 | ND 通告的 IPv6 的 DNS 服务器地址 |
| Advertise MAC Address | 建议勾选 | ND 通告中将包含接口的 MAC 地址信息 |
| Advertise DNS | 必须勾选 | ND 通告中将包含指定的 DNS 服务器 |
 | ||
| 也可以添加公共的IPV6 DNS服务器 |
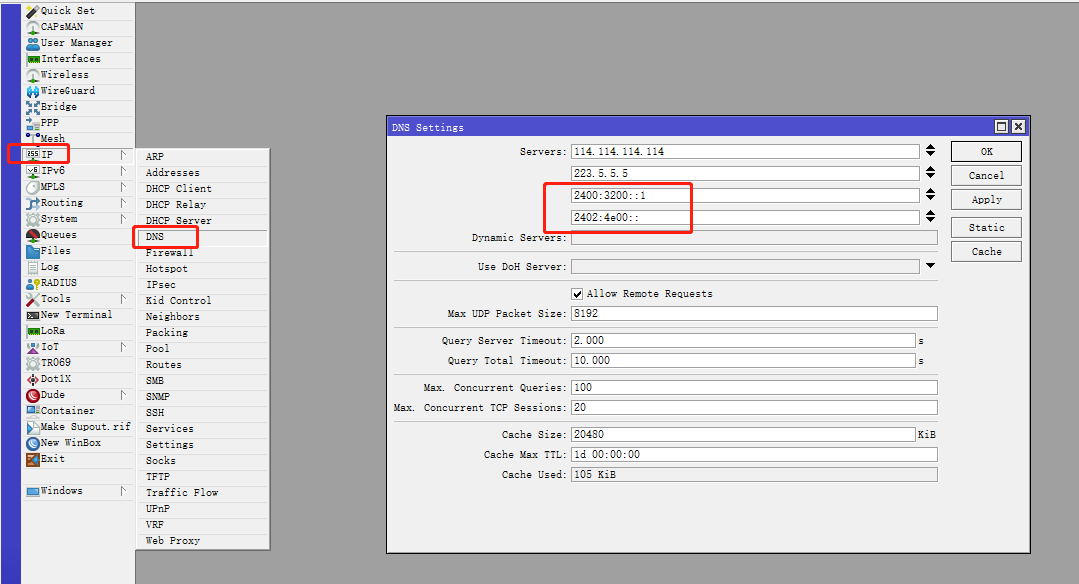
7. 修改系统DNS
修改系统 DNS
启用 IPv6 后,需要给 RouterOS 重新指定上游 DNS 服务器地址。
点击 Winbox 左侧导航 IP 菜单的子菜单 DNS ,并修改 Servers 参数。
在 Servers 处增加国内知名的 DNS 服务提供商的 IPv6 地址。
腾讯云 DNSPod 的 IPv6 地址为:2402:4e00::和 2402:4e00:1::
阿里云 AliDNS 的 IPv6 地址为:2400:3200::1 和 2400:3200:baba::1
8. 设置IPv6防火墙
IPv6 防火墙同样涉及 address-list 、filter 、nat 、mangle 、raw 等内容。
依然建议复制防火墙配置命令,一次性全部粘贴到 CLI 中进行 “一键配置” 。
如果需要使用 NAT66 来访问外部 IPv6 网络,请在 nat 表中启用第一条防火墙规则。
由于防火墙的配置命令很长,因此请根据实际情况选择对应的 IPv6 防火墙配置脚本。
| 联网模式 | 内网DNS | 防火墙模式 |
|---|---|---|
| PPPOE | 否 | 高级 |
代码如下:
## Filter 规则 18 条
## NAT 规则 3 条
## Mangle 规则 1 条
## Raw 规则 48 条
## Address-list 规则 17 条
/ipv6 firewall address-list
add address=fe80::/10 comment="defconf: RFC6890 Linked-Scoped Unicast" list=no_forward_ipv6
add address=ff00::/8 comment="defconf: multicast" list=no_forward_ipv6
add address=::1/128 comment="defconf: RFC6890 lo" list=bad_ipv6
add address=::ffff:0:0/96 comment="defconf: RFC6890 IPv4 mapped" list=bad_ipv6
add address=2001::/23 comment="defconf: RFC6890" list=bad_ipv6
add address=2001:db8::/32 comment="defconf: RFC6890 documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: RFC6890 orchid" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: RFC6890 Discard-only" list=not_global_ipv6
add address=2001::/32 comment="defconf: RFC6890 TEREDO" list=not_global_ipv6
add address=2001:2::/48 comment="defconf: RFC6890 Benchmark" list=not_global_ipv6
add address=fc00::/7 comment="defconf: RFC6890 Unique-Local" list=not_global_ipv6
add address=::/128 comment="defconf: unspecified" list=bad_dst_ipv6
add address=::/128 comment="defconf: unspecified" list=bad_src_ipv6
add address=ff00::/8 comment="defconf: multicast" list=bad_src_ipv6
add address=::/128 comment="ddosconf: DDoS" list=ddos_targets_ipv6
add address=::/128 comment="ddosconf: DDoS" list=ddos_attackers_ipv6
/ipv6 firewall filter
add action=accept chain=input comment="defconf: accept ICMPv6 after RAW" protocol=icmpv6
add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept UDP traceroute" port=33434-33534 protocol=udp
add action=accept chain=input comment="defconf: accept DHCPv6-Client prefix delegation" dst-port=546 protocol=udp src-address=fe80::/10 log=yes log-prefix="[ipv6-pd]"
add action=drop chain=input comment="defconf: drop all not coming from LAN" in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop bad forward IPs" src-address-list=no_forward_ipv6
add action=drop chain=forward comment="defconf: drop bad forward IPs" dst-address-list=no_forward_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6 after RAW" protocol=icmpv6
add action=drop chain=forward comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN
add action=jump chain=forward comment="ddosconf: DDoS" connection-state=new jump-target=detect-ddos
add action=return chain=detect-ddos comment="ddosconf: DDoS SYN-ACK Flood" dst-limit=50,50,src-and-dst-addresses/10s protocol=tcp tcp-flags=syn,ack log=yes log-prefix="[syn-ack-flood]"
add action=return chain=detect-ddos comment="ddosconf: DDoS" dst-limit=200,200,src-and-dst-addresses/10s
add action=add-dst-to-address-list chain=detect-ddos comment="ddosconf: DDoS" address-list=ddos_targets_ipv6 address-list-timeout=10m
add action=add-src-to-address-list chain=detect-ddos comment="ddosconf: DDoS" address-list=ddos_attackers_ipv6 address-list-timeout=10m log=yes log-prefix="[ddos-ipv6]"
/ipv6 firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade IPv6" out-interface-list=WAN disabled=yes
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (UDP)" dst-port=53 in-interface-list=LAN protocol=udp to-ports=53
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (TCP)" dst-port=53 in-interface-list=LAN protocol=tcp to-ports=53
/ipv6 firewall mangle
add action=change-mss chain=forward comment="defconf: fix IPv6 mss for WAN" new-mss=clamp-to-pmtu passthrough=yes protocol=tcp tcp-flags=syn
/ipv6 firewall raw
add action=accept chain=prerouting comment="defconf: enable for transparent firewall" disabled=yes
add action=drop chain=prerouting comment="ddosconf: DDoS" dst-address-list=ddos_targets_ipv6 src-address-list=ddos_attackers_ipv6
add action=drop chain=prerouting comment="defconf: drop IPv6 extension headers types 0,43" headers=hop,route:contains
add action=accept chain=prerouting comment="defconf: RFC4291, section 2.7.1" dst-address=ff02:0:0:0:0:1:ff00::/104 icmp-options=135 protocol=icmpv6 src-address=::/128
add action=drop chain=prerouting comment="defconf: drop bogon IPs" src-address-list=bad_ipv6
add action=drop chain=prerouting comment="defconf: drop bogon IPs" dst-address-list=bad_ipv6
add action=drop chain=prerouting comment="defconf: drop packets with bad SRC ipv6" src-address-list=bad_src_ipv6
add action=drop chain=prerouting comment="defconf: drop packets with bad DST ipv6" dst-address-list=bad_dst_ipv6
add action=drop chain=prerouting comment="defconf: drop non global from WAN" in-interface-list=WAN src-address-list=not_global_ipv6
add action=drop chain=prerouting comment="defconf: drop UDP port 0" port=0 protocol=udp log=yes log-prefix="[udp-port-0]"
add action=jump chain=prerouting comment="defconf: jump to ICMPv6 chain" jump-target=icmp6 protocol=icmpv6
add action=jump chain=prerouting comment="defconf: jump to TCP chain" jump-target=bad-tcp protocol=tcp
add action=accept chain=prerouting comment="defconf: accept local multicast scope" dst-address=ff02::/16
add action=drop chain=prerouting comment="defconf: drop other multicast destinations" dst-address=ff00::/8
add action=accept chain=prerouting comment="defconf: accept everything else from LAN" in-interface-list=LAN
add action=accept chain=prerouting comment="defconf: accept everything else from WAN" in-interface-list=WAN
add action=drop chain=prerouting comment="defconf: drop the rest"
add action=drop chain=bad-tcp comment="defconf: TCP flag filter" protocol=tcp tcp-flags=!fin,!syn,!rst,!ack
add action=drop chain=bad-tcp comment="defconf: drop flags fin,syn" protocol=tcp tcp-flags=fin,syn
add action=drop chain=bad-tcp comment="defconf: drop flags fin,rst" protocol=tcp tcp-flags=fin,rst
add action=drop chain=bad-tcp comment="defconf: drop flags fin,!ack" protocol=tcp tcp-flags=fin,!ack
add action=drop chain=bad-tcp comment="defconf: drop flags fin,urg" protocol=tcp tcp-flags=fin,urg
add action=drop chain=bad-tcp comment="defconf: drop flags syn,rst" protocol=tcp tcp-flags=syn,rst
add action=drop chain=bad-tcp comment="defconf: drop flags rst,urg" protocol=tcp tcp-flags=rst,urg
add action=drop chain=bad-tcp comment="defconf: drop TCP port 0" port=0 protocol=tcp log=yes log-prefix="[tcp-port-0]"
add action=accept chain=icmp6 comment="defconf: rfc4890 drop ll if hop-limit!=255" dst-address=fe80::/10 hop-limit=not-equal:255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 DST unreachable" icmp-options=1:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 packet too big" icmp-options=2:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 time exceeded" icmp-options=3:0-1 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 parameter problem" icmp-options=4:0-2 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 echo request" icmp-options=128:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 echo response" icmp-options=129:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query only LAN" src-address=fe80::/10 icmp-options=130:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query report only LAN" src-address=fe80::/10 icmp-options=131:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query done only LAN" src-address=fe80::/10 icmp-options=132:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 router solic only LAN" hop-limit=equal:255 icmp-options=133:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 router advert only LAN" hop-limit=equal:255 icmp-options=134:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 neighbor solic only LAN" hop-limit=equal:255 icmp-options=135:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 neighbor advert only LAN" hop-limit=equal:255 icmp-options=136:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 inverse ND solic only LAN" hop-limit=equal:255 icmp-options=141:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 inverse ND advert only LAN" hop-limit=equal:255 icmp-options=142:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener report v2 only LAN" src-address=fe80::/10 icmp-options=143:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 certificate path solicitation only LAN" hop-limit=equal:255 icmp-options=148:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 certificate path advertisement only LAN" hop-limit=equal:255 icmp-options=149:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router advertisement only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=151:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router solicitation only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=152:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router termination only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=153:0-255 in-interface-list=LAN protocol=icmpv6
add action=drop chain=icmp6 comment="defconf: drop all other ICMPv6" protocol=icmpv6
| 联网模式 | 内网DNS | 防火墙模式 |
|---|---|---|
| PPPOE | 是 | 高级 |
代码如下:
## Filter 规则 18 条
## NAT 规则 5 条
## Mangle 规则 1 条
## Raw 规则 48 条
## Address-list 规则 18 条
/ipv6 firewall address-list
add address=fc00::1 comment="lanconf: local DNS server" list=local_dns_ipv6
add address=fe80::/10 comment="defconf: RFC6890 Linked-Scoped Unicast" list=no_forward_ipv6
add address=ff00::/8 comment="defconf: multicast" list=no_forward_ipv6
add address=::1/128 comment="defconf: RFC6890 lo" list=bad_ipv6
add address=::ffff:0:0/96 comment="defconf: RFC6890 IPv4 mapped" list=bad_ipv6
add address=2001::/23 comment="defconf: RFC6890" list=bad_ipv6
add address=2001:db8::/32 comment="defconf: RFC6890 documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: RFC6890 orchid" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: RFC6890 Discard-only" list=not_global_ipv6
add address=2001::/32 comment="defconf: RFC6890 TEREDO" list=not_global_ipv6
add address=2001:2::/48 comment="defconf: RFC6890 Benchmark" list=not_global_ipv6
add address=fc00::/7 comment="defconf: RFC6890 Unique-Local" list=not_global_ipv6
add address=::/128 comment="defconf: unspecified" list=bad_dst_ipv6
add address=::/128 comment="defconf: unspecified" list=bad_src_ipv6
add address=ff00::/8 comment="defconf: multicast" list=bad_src_ipv6
add address=::/128 comment="ddosconf: DDoS" list=ddos_targets_ipv6
add address=::/128 comment="ddosconf: DDoS" list=ddos_attackers_ipv6
/ipv6 firewall filter
add action=accept chain=input comment="defconf: accept ICMPv6 after RAW" protocol=icmpv6
add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept UDP traceroute" port=33434-33534 protocol=udp
add action=accept chain=input comment="defconf: accept DHCPv6-Client prefix delegation" dst-port=546 protocol=udp src-address=fe80::/10 log=yes log-prefix="[ipv6-pd]"
add action=drop chain=input comment="defconf: drop all not coming from LAN" in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop bad forward IPs" src-address-list=no_forward_ipv6
add action=drop chain=forward comment="defconf: drop bad forward IPs" dst-address-list=no_forward_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6 after RAW" protocol=icmpv6
add action=drop chain=forward comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN
add action=jump chain=forward comment="ddosconf: DDoS" connection-state=new jump-target=detect-ddos
add action=return chain=detect-ddos comment="ddosconf: DDoS SYN-ACK Flood" dst-limit=50,50,src-and-dst-addresses/10s protocol=tcp tcp-flags=syn,ack log=yes log-prefix="[syn-ack-flood]"
add action=return chain=detect-ddos comment="ddosconf: DDoS" dst-limit=200,200,src-and-dst-addresses/10s
add action=add-dst-to-address-list chain=detect-ddos comment="ddosconf: DDoS" address-list=ddos_targets_ipv6 address-list-timeout=10m
add action=add-src-to-address-list chain=detect-ddos comment="ddosconf: DDoS" address-list=ddos_attackers_ipv6 address-list-timeout=10m log=yes log-prefix="[ddos-ipv6]"
/ipv6 firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade IPv6" out-interface-list=WAN disabled=yes
add action=accept chain=dstnat comment="lanconf: accept local DNS server's query (UDP)" dst-port=53 in-interface-list=LAN protocol=udp src-address-list=local_dns_ipv6
add action=accept chain=dstnat comment="lanconf: accept local DNS server's query (TCP)" dst-port=53 in-interface-list=LAN protocol=tcp src-address-list=local_dns_ipv6
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (UDP)" dst-port=53 in-interface-list=LAN protocol=udp to-ports=53
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (TCP)" dst-port=53 in-interface-list=LAN protocol=tcp to-ports=53
/ipv6 firewall mangle
add action=change-mss chain=forward comment="defconf: fix IPv6 mss for WAN" new-mss=clamp-to-pmtu passthrough=yes protocol=tcp tcp-flags=syn
/ipv6 firewall raw
add action=accept chain=prerouting comment="defconf: enable for transparent firewall" disabled=yes
add action=drop chain=prerouting comment="ddosconf: DDoS" dst-address-list=ddos_targets_ipv6 src-address-list=ddos_attackers_ipv6
add action=drop chain=prerouting comment="defconf: drop IPv6 extension headers types 0,43" headers=hop,route:contains
add action=accept chain=prerouting comment="defconf: RFC4291, section 2.7.1" dst-address=ff02:0:0:0:0:1:ff00::/104 icmp-options=135 protocol=icmpv6 src-address=::/128
add action=drop chain=prerouting comment="defconf: drop bogon IPs" src-address-list=bad_ipv6
add action=drop chain=prerouting comment="defconf: drop bogon IPs" dst-address-list=bad_ipv6
add action=drop chain=prerouting comment="defconf: drop packets with bad SRC ipv6" src-address-list=bad_src_ipv6
add action=drop chain=prerouting comment="defconf: drop packets with bad DST ipv6" dst-address-list=bad_dst_ipv6
add action=drop chain=prerouting comment="defconf: drop non global from WAN" in-interface-list=WAN src-address-list=not_global_ipv6
add action=drop chain=prerouting comment="defconf: drop UDP port 0" port=0 protocol=udp log=yes log-prefix="[udp-port-0]"
add action=jump chain=prerouting comment="defconf: jump to ICMPv6 chain" jump-target=icmp6 protocol=icmpv6
add action=jump chain=prerouting comment="defconf: jump to TCP chain" jump-target=bad-tcp protocol=tcp
add action=accept chain=prerouting comment="defconf: accept local multicast scope" dst-address=ff02::/16
add action=drop chain=prerouting comment="defconf: drop other multicast destinations" dst-address=ff00::/8
add action=accept chain=prerouting comment="defconf: accept everything else from LAN" in-interface-list=LAN
add action=accept chain=prerouting comment="defconf: accept everything else from WAN" in-interface-list=WAN
add action=drop chain=prerouting comment="defconf: drop the rest"
add action=drop chain=bad-tcp comment="defconf: TCP flag filter" protocol=tcp tcp-flags=!fin,!syn,!rst,!ack
add action=drop chain=bad-tcp comment="defconf: drop flags fin,syn" protocol=tcp tcp-flags=fin,syn
add action=drop chain=bad-tcp comment="defconf: drop flags fin,rst" protocol=tcp tcp-flags=fin,rst
add action=drop chain=bad-tcp comment="defconf: drop flags fin,!ack" protocol=tcp tcp-flags=fin,!ack
add action=drop chain=bad-tcp comment="defconf: drop flags fin,urg" protocol=tcp tcp-flags=fin,urg
add action=drop chain=bad-tcp comment="defconf: drop flags syn,rst" protocol=tcp tcp-flags=syn,rst
add action=drop chain=bad-tcp comment="defconf: drop flags rst,urg" protocol=tcp tcp-flags=rst,urg
add action=drop chain=bad-tcp comment="defconf: drop TCP port 0" port=0 protocol=tcp log=yes log-prefix="[tcp-port-0]"
add action=accept chain=icmp6 comment="defconf: rfc4890 drop ll if hop-limit!=255" dst-address=fe80::/10 hop-limit=not-equal:255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 DST unreachable" icmp-options=1:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 packet too big" icmp-options=2:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 time exceeded" icmp-options=3:0-1 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 parameter problem" icmp-options=4:0-2 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 echo request" icmp-options=128:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 echo response" icmp-options=129:0-255 protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query only LAN" src-address=fe80::/10 icmp-options=130:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query report only LAN" src-address=fe80::/10 icmp-options=131:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener query done only LAN" src-address=fe80::/10 icmp-options=132:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 router solic only LAN" hop-limit=equal:255 icmp-options=133:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 router advert only LAN" hop-limit=equal:255 icmp-options=134:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 neighbor solic only LAN" hop-limit=equal:255 icmp-options=135:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 neighbor advert only LAN" hop-limit=equal:255 icmp-options=136:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 inverse ND solic only LAN" hop-limit=equal:255 icmp-options=141:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 inverse ND advert only LAN" hop-limit=equal:255 icmp-options=142:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast listener report v2 only LAN" src-address=fe80::/10 icmp-options=143:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 certificate path solicitation only LAN" hop-limit=equal:255 icmp-options=148:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 certificate path advertisement only LAN" hop-limit=equal:255 icmp-options=149:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router advertisement only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=151:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router solicitation only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=152:0-255 in-interface-list=LAN protocol=icmpv6
add action=accept chain=icmp6 comment="defconf: rfc4890 multicast router termination only LAN" src-address=fe80::/10 hop-limit=equal:1 icmp-options=153:0-255 in-interface-list=LAN protocol=icmpv6
add action=drop chain=icmp6 comment="defconf: drop all other ICMPv6" protocol=icmpv6
| 联网模式 | 内网DNS | 防火墙模式 |
|---|---|---|
| PPPOE | 否 | 精简 |
点击复制代码
## Filter 规则 13 条
## NAT 规则 3 条
## Mangle 规则 1 条
## Address-list 规则 9 条
/ipv6 firewall address-list
add list=bad_ipv6 address=::/128 comment="defconf: unspecified address"
add list=bad_ipv6 address=::1 comment="defconf: lo"
add list=bad_ipv6 address=fec0::/10 comment="defconf: site-local"
add list=bad_ipv6 address=::ffff:0:0/96 comment="defconf: ipv4-mapped"
add list=bad_ipv6 address=::/96 comment="defconf: ipv4 compat"
add list=bad_ipv6 address=100::/64 comment="defconf: discard only "
add list=bad_ipv6 address=2001:db8::/32 comment="defconf: documentation"
add list=bad_ipv6 address=2001:10::/28 comment="defconf: ORCHID"
add list=bad_ipv6 address=3ffe::/16 comment="defconf: 6bone"
/ipv6 firewall filter
add chain=input action=accept connection-state=established,related,untracked comment="defconf: accept established,related,untracked"
add chain=input action=drop connection-state=invalid comment="defconf: drop invalid"
add chain=input action=accept protocol=icmpv6 comment="defconf: accept ICMPv6"
add chain=input action=accept protocol=udp port=33434-33534 comment="defconf: accept UDP traceroute"
add chain=input action=accept protocol=udp dst-port=546 src-address=fe80::/10 comment="defconf: accept DHCPv6-Client prefix delegation" log=yes log-prefix="[ipv6-pd]"
add chain=input action=drop in-interface-list=!LAN comment="defconf: drop everything else not coming from LAN"
add chain=forward action=accept connection-state=established,related,untracked comment="defconf: accept established,related,untracked"
add chain=forward action=drop connection-state=invalid comment="defconf: drop invalid"
add chain=forward action=drop src-address-list=bad_ipv6 comment="defconf: drop packets with bad src ipv6"
add chain=forward action=drop dst-address-list=bad_ipv6 comment="defconf: drop packets with bad dst ipv6"
add chain=forward action=drop protocol=icmpv6 hop-limit=equal:1 comment="defconf: rfc4890 drop hop-limit=1"
add chain=forward action=accept protocol=icmpv6 comment="defconf: accept ICMPv6"
add chain=forward action=drop in-interface-list=!LAN comment="defconf: drop everything else not coming from LAN"
/ipv6 firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade IPv6" out-interface-list=WAN disabled=yes
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (UDP)" dst-port=53 in-interface-list=LAN protocol=udp to-ports=53
add action=redirect chain=dstnat comment="lanconf: redirect DNS query (TCP)" dst-port=53 in-interface-list=LAN protocol=tcp to-ports=53
/ipv6 firewall mangle
add action=change-mss chain=forward comment="defconf: fix IPv6 mss for WAN" new-mss=clamp-to-pmtu passthrough=yes protocol=tcp tcp-flags=syn
- 防火墙配置命令中的部分 IPv6 ULA 地址需要根据实际情况进行调整。
- 内网使用的 IPv6 ULA 地址前缀 fc00::/64
- RouterOS 的 IPv6 ULA 地址 fc00::1
- 内网 DNS 服务器的 IPv6 ULA 地址 fc00::2
- IPv6 防火墙配置完成后,回到 Winbox,点击左侧导航 IPv6 菜单的子菜单 Firewall 并查看防火墙各个选项卡中内容。
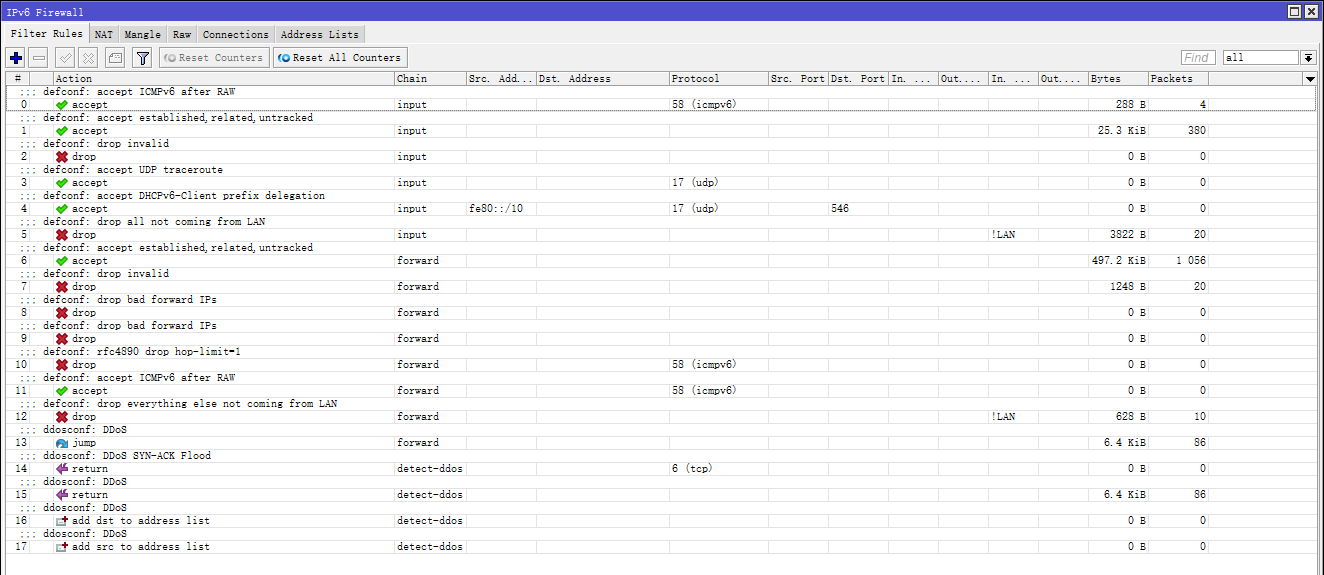
确认防火墙条目与命令中的条目一致后,便可启用 IPv6 的 DHCPv6 Client ,建议重启一次 RouterOS。
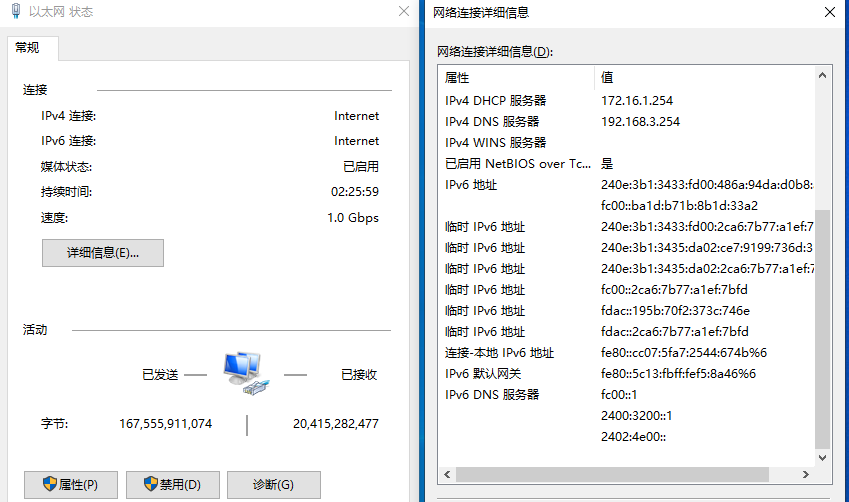
重启内网设备的网卡,检查是否获取了 GUA / ULA 地址。
Windows10 IPv6 连接处会显示 Internet ,表示此时 Windows 是可以访问 IPv6 网络的。
可以通过这个网站来进行测试 IPv6 Test 。
设置 IPv6 黑洞路由
IPv6 黑洞路由 blackhole route 是一组静态路由,基于 RFC6890 - Special-Purpose IP Address Registries 创建。
配置 IPv6 黑洞路由时,将以下命令一次性全部粘贴到 CLI 中执行即可。
/ipv6 route
add blackhole comment="defconf: RFC6890 - loopback address" disabled=no dst-address=::1/128
add blackhole comment="defconf: RFC6890 - unspecified address" disabled=no dst-address=::/128
add blackhole comment="defconf: RFC6890 - IPv4-IPv6 translate" disabled=no dst-address=64:ff9b::/96
add blackhole comment="defconf: RFC6890 - IPv4-mapped address" disabled=no dst-address=::ffff:0:0/96
add blackhole comment="defconf: RFC6890 - discard-only address block" disabled=no dst-address=100::/64
add blackhole comment="defconf: RFC6890 - IETF protocol assignments" disabled=no dst-address=2001::/23
add blackhole comment="defconf: RFC6890 - TEREDO" disabled=no dst-address=2001::/32
add blackhole comment="defconf: RFC6890 - benchmarking" disabled=no dst-address=2001:2::/48
add blackhole comment="defconf: RFC6890 - documentation" disabled=no dst-address=2001:db8::/32
add blackhole comment="defconf: RFC6890 - ORCHID" disabled=no dst-address=2001:10::/28
add blackhole comment="defconf: RFC6890 - 6to4" disabled=no dst-address=2002::/16
add blackhole comment="defconf: RFC6890 - unique-local" disabled=no dst-address=fc00::/7
add blackhole comment="defconf: RFC6890 - linked-scoped unicast" disabled=no dst-address=fe80::/10
点击 Winbox 左侧导航 IP 菜单的子菜单 Routes 并查看防火墙各个选项卡中内容。
至此,RouterOS 设置 IPv6 步骤完成。